What is Zero Trust Security? A Simple Guide to Getting Started
As cyberattacks evolve, perimeter-based security is failing. Enter Zero Trust, a modern framework built on ‘never trust, always verify.’ This article details what Zero Trust is and the steps to implement it.
What is Zero Trust Security? A Simple Guide to Getting Started
Table of Contents
Let's be honest, the old "castle-and-moat" approach to cybersecurity just isn't cutting it anymore. With cyber threats getting smarter, simply trusting everyone inside your network is a recipe for disaster. That’s why a new philosophy is taking over: Zero Trust. It’s built on a simple but powerful idea: "never trust, always verify." This guide will break down what Zero Trust is, why your business needs it, and how you can start putting it into practice today.
Contact:- sales@bminfotradegroup.com +919314508367 / +919829189200
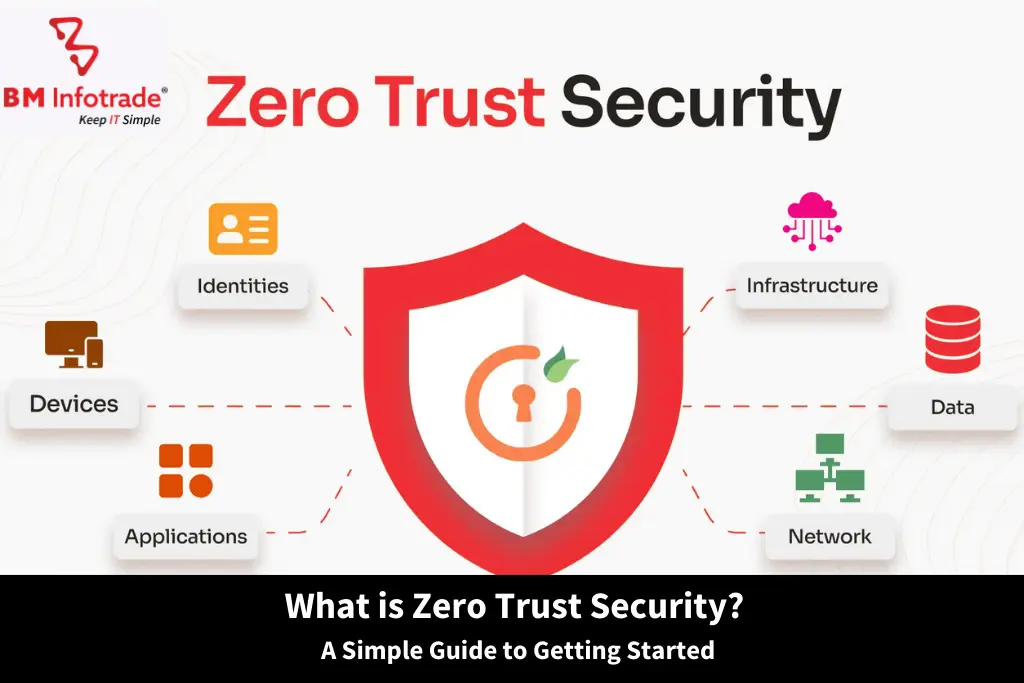
What Is Zero Trust Security?
Think of Zero Trust like a strict security guard for your digital assets. It doesn't matter if you're an employee, a partner, or a top executive—no one gets a free pass. Every single time someone or something tries to access your data or applications, Zero Trust stops them and asks, "Who are you, and should you really be here?" Unlike old-school security that focused on protecting the "perimeter," Zero Trust assumes threats could be anywhere, both inside and outside your network.
In short, with Zero Trust:
- Trust is never assumed for any user or device.
- Access depends on identity, context, and behavior.
- Every single request to access something is logged, authenticated, and checked.
Why the Old Way Doesn't Work Anymore
The old security model worked when everyone was in the office, using company-owned computers. Once you were "in" the network (maybe through a VPN), you could access almost everything. That model is broken now because:
- People are working from anywhere, on any device.
- Your apps and data are scattered across different cloud services.
- Insider threats, whether accidental or malicious, are a huge risk.
- Credential-based attacks are on the rise.
In today's world, a single stolen password or a compromised laptop could give an attacker the keys to your entire kingdom.
The Core Ideas Behind Zero Trust
To make Zero Trust work, you need to embrace a few key principles:
-
Verify Everything, Every Time: Always confirm user identities and device health before granting access. This means looking at multiple signals like location, device type, and user behavior.
-
Give Only Necessary Access: This is the principle of least privilege. Users only get access to the specific data and tools they absolutely need to do their jobs, and nothing more. This limits the damage if an account is compromised.
-
Assume You've Already Been Breached: This mindset shifts your focus from just prevention to rapid detection and response. You're always on the lookout for threats already inside your network.
-
Monitor Continuously: Verification isn't a one-time event. You need to constantly monitor sessions for any strange behavior and be ready to automatically end access if something seems off.
-
Break Up Your Network (Micro-segmentation): Imagine your network is a building. Instead of one big open floor, you create many small, locked rooms. If one room is breached, the rest of the building remains secure.

What's in It for You? The Benefits of Zero Trust
Adopting a Zero Trust model brings some serious advantages:
-
Stronger Data Protection: It offers far better protection against both outside hackers and insider threats.
-
Reduced Attack Surface: If an attacker does get in, they're contained in a small area and can't move freely across your network.
-
Smarter Access Controls: You can create specific, context-aware rules for who can access what, and when.
-
Easier Compliance: It helps you meet strict data protection regulations like GDPR, HIPAA, and NIST.
-
Secure Remote Work: It's the perfect security model for today's hybrid and remote workforces, where you have less control over networks and devices.
Read More:- Top 10 Indian Companies Offering 24x7 SOC Services in INDIA
Contact:- sales@bminfotradegroup.com +919314508367 / +919829189200
Be Prepared for These Challenges
Shifting to Zero Trust isn't an overnight project. It's a journey, and you'll likely face a few hurdles:
-
It's a Big Project: Implementing Zero Trust often requires rethinking parts of your IT infrastructure and policies.
-
Too Many Tools: Many vendors claim to offer a "Zero Trust solution," but there's no single product that does it all. You'll need a combination of tools.
-
Getting Your Team on Board: Some employees might find new security steps, like extra authentication, a bit frustrating at first.
-
Dealing with Old Tech: Your older, legacy systems might not support the modern security controls needed for Zero Trust.
The key is to take it one step at a time.
Your 7-Step Roadmap to Zero Trust
Ready to get started? Here’s a practical, step-by-step guide to begin your Zero Trust journey.
Step 1: Know What You're Protecting
First, you need a clear inventory of your users, devices, apps, and data. Figure out what your most critical assets are, who needs to access them, and where they live (on-premise, in the cloud, or both).
Step 2: Double Down on Identity
Zero Trust begins with knowing who is asking for access. Your top priority should be strengthening your identity controls.
-
Implement Multi-Factor Authentication (MFA) everywhere.
-
Use Single Sign-On (SSO) to simplify and secure user access.
-
Set up Conditional Access Policies that grant access based on risk signals.
Step 3: Don't Trust Any Device
Only secure and healthy devices should be allowed to connect. Use endpoint management tools to check that devices are encrypted, have up-to-date antivirus software, and aren't jailbroken or compromised.
Step 4: Create Secure Zones (Micro-segmentation)
Divide your network into smaller, isolated segments. This ensures that someone in the HR department can't access engineering servers, and vice-versa. If one zone is compromised, the others stay safe.
Step 5: Watch Everything in Real-Time
You can't stop what you can't see. Deploy tools that give you visibility into all network traffic, user activity, and access requests. Look for anything out of the ordinary.
Step 6: Automate Your Defenses
Use automation to respond to threats instantly. For example, you can automatically lock an account after too many failed login attempts or trigger a re-authentication request if a user suddenly logs in from a new country.
Step 7: Make Security a Team Sport
Your employees are your first line of defense. Train them to spot phishing emails, understand the importance of security protocols like MFA, and report anything suspicious.
Conclusion
Zero Trust is more than just a buzzword—it's a fundamental shift in how we approach cybersecurity in a world of remote work and cloud-based everything. While it might seem like a huge undertaking, you don't have to do it all at once. Start by focusing on your most critical assets and build from there. The goal is to create a security culture where trust is never assumed and every access request is verified.
Contact:- sales@bminfotradegroup.com +919314508367 / +919829189200
FAQs
1. How is Zero Trust different from traditional security like firewalls and VPNs?
Traditional security operates like a castle with a moat; once you're inside the network (often via a VPN), you are trusted and can access many resources freely. Zero Trust, on the other hand, assumes that threats can exist both inside and outside the network. It trusts no one by default. Every single access request is verified every time, regardless of who or what is asking.
2. Is Zero Trust a single product I can buy and install?
No, Zero Trust is not a single product you can purchase. It is a security framework and a strategic approach. While many vendors offer tools that support Zero Trust principles—such as multi-factor authentication (MFA) or identity management systems—a complete implementation requires a combination of different technologies, policies, and processes working together.
3. Will implementing Zero Trust make it harder for my employees to do their jobs?
When implemented correctly, Zero Trust should enhance security without creating significant disruptions for users. While there might be an adjustment period as employees get used to new measures like MFA, the goal is a seamless experience. Modern tools like Single Sign-On (SSO) can actually simplify access, while risk-based policies ensure that users are only prompted for extra verification when behavior seems unusual.
4. What is the most important first step to start our Zero Trust journey?
The most critical first step is to strengthen your identity and access management (IAM). Before anything else, focus on implementing Multi-Factor Authentication (MFA) for all users. Identity is the new security perimeter, and ensuring you can verify every user with high confidence is the foundation of the entire Zero Trust model.
5. How does Zero Trust help prevent ransomware attacks?
Zero Trust is highly effective at containing ransomware. By using principles like least-privilege access and micro-segmentation, it limits an attacker's ability to move laterally across your network. If a device gets infected with ransomware, it is isolated within its small network segment, preventing the malware from spreading to critical systems and data.



![Cloud Licensing and Compliance Made Easy [All-in-One Bundle]](https://www.bminfotrade.com/public/assets/upload/blog/21851766642757.png)

Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader